A Verkle tree is a dedication scheme that works much like a Merkle tree, however has a lot smaller witnesses. It really works by changing the hashes in a Merkle tree with a vector dedication, which makes wider branching elements extra environment friendly.
Due to Kevaundray Wedderburn for suggestions on the submit.
Overview
For particulars on how verkle timber work, see:
The purpose of this submit is to clarify the concrete format of the draft verkle tree EIP. It’s aimed toward consumer builders who need to implement verkle timber and are in search of an introduction earlier than delving deeper into the EIP.
Verkle timber introduce numerous adjustments to the tree construction. Essentially the most vital adjustments are:
- a swap from 20 byte keys to 32 byte keys (to not be confused with 32 byte addresses, which is a separate change);
- the merge of the account and storage tries; and at last
- The introduction of the verkle trie itself, which makes use of vector commitments as an alternative of hashes.
Because the vector dedication scheme for the verkle tree, we use Pedersen commitments. Pedersen commitments are based mostly on elliptic curves. For an introduction to Pedersen commitments and tips on how to use them as polynomial or vector commitments utilizing Interior Product Argumentss, see here.
The curve we’re utilizing is Bandersnatch. This curve was chosen as a result of it’s performant, and in addition as a result of it would enable environment friendly SNARKs in BLS12_381 to cause concerning the verkle tree sooner or later. This may be helpful for rollups in addition to permitting an improve the place all witnesses might be compressed into one SNARK as soon as that turns into sensible, while not having an additional dedication replace.
The curve order/scalar area dimension of bandersnatch is p = 13108968793781547619861935127046491459309155893440570251786403306729687672801, which is a 253 bit prime. Because of this, we will solely safely decide to bit strings of at most 252 bits, in any other case the sector overflows. We selected a branching issue (width) of 256 for the verkle tree, which implies every dedication can decide to as much as 256 values of 252 bits every (or to be exact, integers as much as p – 1). We write this as Commit(v₀, v₁, …, v₂₅₅) to decide to the record v of size 256.
Structure of the verkle tree
One of many design objectives with the verkle tree EIP is to make accesses to neighbouring positions (e.g. storage with nearly the identical deal with or neighbouring code chunks) low cost to entry. So as to do that, a key consists of a stem of 31 bytes and a suffix of 1 byte for a complete of 32 bytes. The important thing scheme is designed in order that “shut” storage places are mapped to the identical stem and a unique suffix. For particulars please take a look at the EIP draft.
The verkle tree itself is then composed of two sorts of nodes:
- Extension nodes, that signify 256 values with the identical stem however completely different suffixes
- Interior nodes, which have as much as 256 youngsters, which might be both different interior nodes or extension nodes.
The dedication to an extension node is a dedication to a 4 ingredient vector; the remaining positions can be 0. It’s:
![]()
C₁ and C₂ are two additional commitments that decide to all of the values with stem equal to stem. The explanation we want two commitments is that values have 32 bytes, however we will solely retailer 252 bits per area ingredient. A single dedication would thus not be sufficient to retailer 256 values. So as an alternative C₁ shops the values for suffix 0 to 127, and C₂ shops 128 to 255, the place the values are cut up in two as a way to match into the sector dimension (we’ll come to that later.)
The extension along with the commitments C₁ and C₂ are known as “extension-and-suffix tree” (EaS for brief).
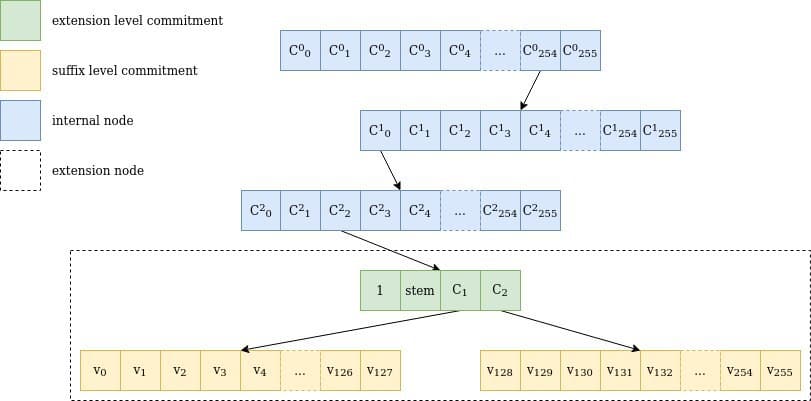
Determine 1 Illustration of a stroll by means of a verkle tree for the important thing 0xfe0002abcd..ff04: the trail goes by means of 3 inside nodes with 256 youngsters every (254, 0, 2), one extension node representing abcd..ff and the 2 suffix tree commitments, together with the worth for 04, v₄. Be aware that stem is definitely the primary 31 bytes of the important thing, together with the trail by means of the inner nodes.
Dedication to the values leaf nodes
Every extension and suffix tree node incorporates 256 values. As a result of a price is 256 bits vast, and we will solely retailer 252 bits safely in a single area ingredient, 4 bits could be misplaced if we merely tried so retailer one worth in a single area ingredient.
To avoid this downside, we selected to partition the group of 256 values into two teams of 128 values every. Every 32-byte worth in a gaggle is cut up into two 16-byte values. So a price vᵢ∈ 𝔹₃₂ is became v⁽ˡᵒʷᵉʳ⁾ᵢ ∈ 𝔹₁₆ and v⁽ᵘᵖᵖᵉʳ⁾ᵢ∈ 𝔹₁₆ such that v⁽ˡᵒʷᵉʳ⁾ᵢ ++ v⁽ᵘᵖᵖᵉʳ⁾ᵢ= vᵢ.
A “leaf marker” is added to the v⁽ˡᵒʷᵉʳ⁾ᵢ, to distinguish between a leaf that has by no means been accessed and a leaf that has been overwritten with 0s. No worth ever will get deleted from a verkle tree. That is wanted for upcoming state expiry schemes. That marker is about on the 129th bit, i.e. v⁽ˡᵒʷᵉʳ ᵐᵒᵈⁱᶠⁱᵉᵈ⁾ᵢ = v⁽ˡᵒʷᵉʳ⁾ᵢ + 2¹²⁸ if vᵢ has been accessed earlier than, and v⁽ˡᵒʷᵉʳ ᵐᵒᵈⁱᶠⁱᵉᵈ⁾ᵢ = 0 if vᵢ has by no means been accessed.
The 2 commitments C₁ and C₂ are then outlined as

Dedication of extension nodes
The dedication to an extension node consists of an “extension marker”, which is simply the #1, the 2 subtree commitments C₁ and C₂, and the stem of the important thing resulting in this extension node.
![]()
Not like extension nodes within the Merkle-Patricia tree, which solely comprise the part of the important thing that bridges the mum or dad inside node to the kid inside node, the stem covers the entire key as much as that time. It’s because verkle timber are designed with stateless proofs in thoughts: if a brand new key’s inserted that “splits” the extension in two, the older sibling needn’t be up to date, which permits for a smaller proof.
Dedication of Inner nodes
Inner nodes have the easier calculation methodology for his or her commitments: the node is seen as a vector of 256 values, which are the (area illustration of the) root dedication of every of their 256 subtrees. The dedication for an empty subtree is 0. If the subtree shouldn’t be empty, then the dedication for the inner node is
![]()
the place the Cᵢ are the kids of the inner node, and 0 if a baby is empty.
Insertion into the tree
Determine 2 is an illustration of the method of inserting a brand new worth into the tree, which will get fascinating when the stems collide on a number of preliminary bytes.
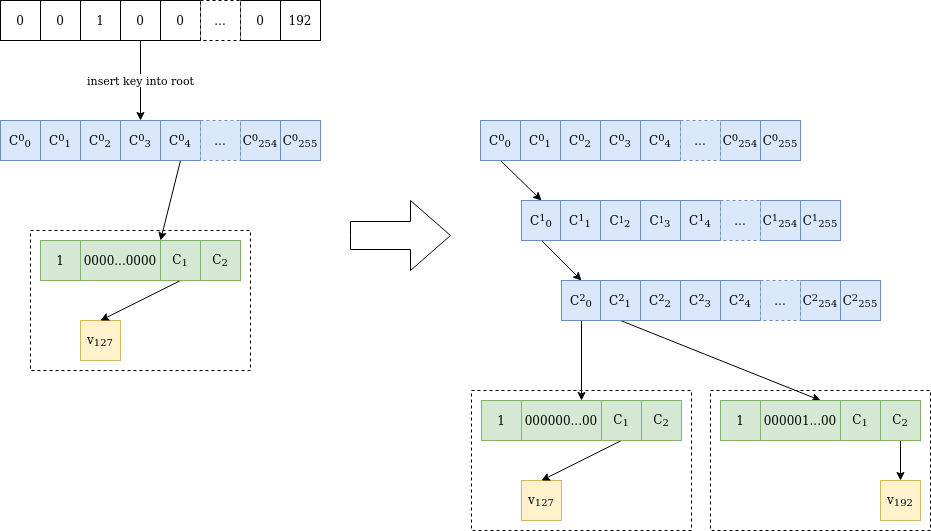
Determine 2 Worth v₁₉₂ is inserted at location 0000010000…0000 in a verkle tree containing solely worth v₁₂₇ at location 0000000000…0000. As a result of the stems differ on the third byte, two inside nodes are added till the differing byte. Then one other “extension-and-suffix” tree is inserted, with a full 31-byte stem. The preliminary node is untouched, and C²₀ has the identical worth as C⁰₀ earlier than the insertion.
Shallower timber, smaller proofs
The verkle tree construction makes for shallower timber, which reduces the quantity of saved knowledge. Its actual energy, nonetheless, comes from the flexibility to supply smaller proofs, i.e. witnesses. This can be defined within the subsequent article.













